As I have previously discussed, there has been an explosion of information and speculation about the Spectre and Meltdown vulnerabilities. Here is the official information about all three vulnerabilities.
Spectre
CVE-2017-5753 (Bounds Check Bypass)
CVE-2017-5715 (Branch Target Injection)
Meltdown
CVE-2017-5754 (Rogue Data Cache Load)
Checking Your Meltdown and Spectre Mitigation Status in Windows
Microsoft has released a PowerShell module that you can easily use to check whether you have the operating system patch that helps mitigate CVE-2017-5715 (Spectre – Branch Target Injection) installed and enabled, along with a BIOS/CPU microcode update that is also required as part of the mitigation.
The script also shows whether you have the operating system patch to mitigate CVE-2017-5754 (Meltdown – Rogue Data Cache Load) installed and enabled, along with whether you have OS support for the PCID performance optimization, which relies on hardware support in your processor for the process-context identifiers (PCID) feature to reduce the performance impact of the CVE-2017-5754 patch.
This Microsoft KB article explains this in more detail and has a link to download the PowerShell Module for operating systems prior to Windows Server 2016.
I have a Dell Precision 5520 laptop with an Intel Xeon E3-1505M v6 processor, running Windows 10 Professional Version 1709 (OS Build 16299.192) with the January 2018 Security Update (KB4056892) installed. I have also installed BIOS version 1.7.0 for the Dell Precision 5520, which has the firmware update to help mitigate CVE-2017-5715.
Figure 1 shows the results I get after installing both of these updates.
Figure 1: Get-SpeculationControlSettings Results on Fully Patched Dell Precision 5520
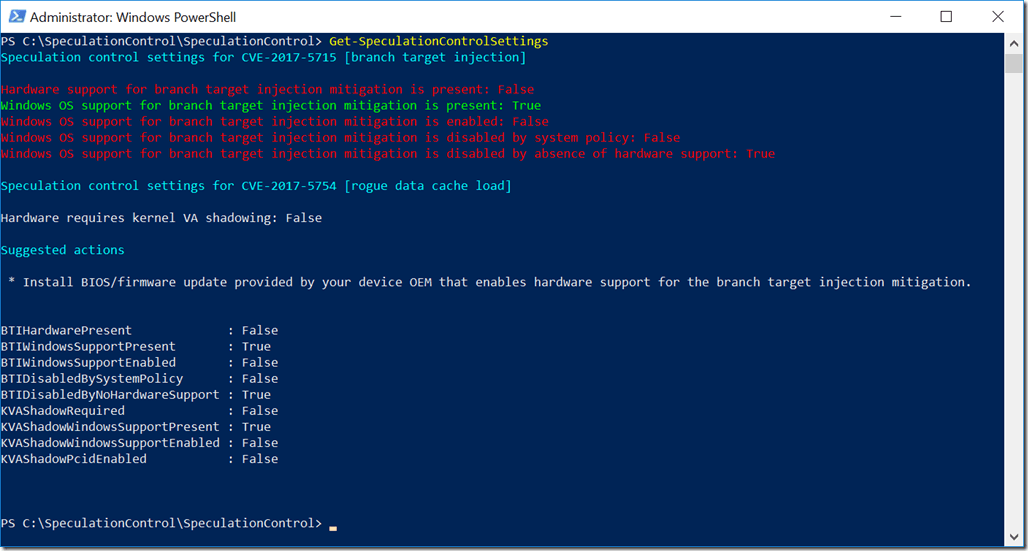
I also have a ASRock Fatal1ty X399 Professional Gaming desktop system with an AMD Ryzen Threadripper 1950X processor, running Windows 10 Professional Version 1709 (OS Build 16299.192) with the January 2018 Security Update (KB4056892) installed. I have the latest BIOS version 2.00 for the ASRock Fatal1ty X399 Professional Gaming (which does not include the CVE-2017-5715 firmware fix). ASRock has not released an updated BIOS for this issue yet.
Figure 2 shows the results after installing the Windows 10 January 2018 Security Update. It is also notable that the Get-SpeculationControlSettings module does not think that this modern AMD processor needs kernel VA shadowing (meaning that it is not vulnerable to CVE-2017-5754).
Figure 2: Get-SpeculationControlSettings Results on Partially Patched ASRock Fatal1ty X399 Professional Gaming
This Microsoft KB article explains in great detail how to interpret the results of Get-SpeculationControlSettings
Understanding Get-SpeculationControlSettings PowerShell script output


3 thoughts on “Checking Your Meltdown and Spectre Mitigation Status in Windows”
Glenn,
Have you had a chance to look at SQL performance yet?
Also it sounds like you are lucky you have a modern AMD processors as it is being reported that older AMD processors are getting BSOD’s after having the Windows patches applied.
Thanks
Chris
If I read this right https://cloudblogs.microsoft.com/microsoftsecure/2018/01/09/understanding-the-performance-impact-of-spectre-and-meltdown-mitigations-on-windows-systems/
badly written queries on older chips could see significant performance drop.
Chris