I have a fairly recent vintage HP Spectre x360-13w023dx laptop (slightly over a year old) that has an Intel Core i7-7500U (Kaby Lake-U) processor, 16GB of DDR4 RAM, and a 512GB Samsung PM961 M.2 NVMe SSD that is running Windows 10 Professional Version 1709.
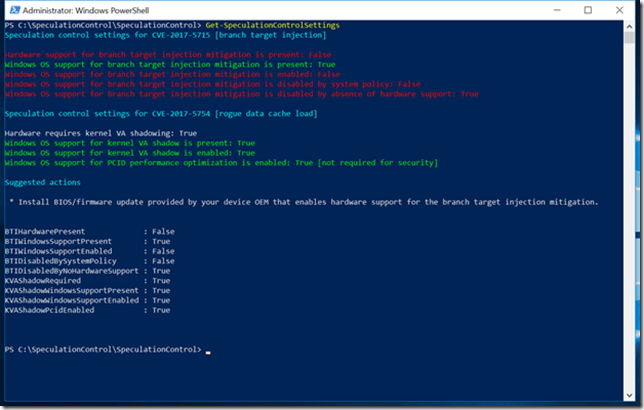
Last night, I installed the Windows 10 January 2018 Security Update (KB4056892) on this system, and then used PowerShell to check my status, with the results as shown in Figure 1. These are the relevant results:
Speculation control settings for CVE-2017-5715 [branch target injection] (This is Spectre variant 2)
Hardware support for branch target injection mitigation is present: False
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: False
Windows OS support for branch target injection mitigation is disabled by system policy: False
Windows OS support for branch target injection mitigation is disabled by absence of hardware support: True
Speculation control settings for CVE-2017-5754 [rogue data cache load] (This is Meltdown)
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: True [not required for security]
Suggested actions
* Install BIOS/firmware update provided by your device OEM that enables hardware support for the branch target injection mitigation mitigation
Figure 1: After Windows 10 Security Update, but before BIOS Update
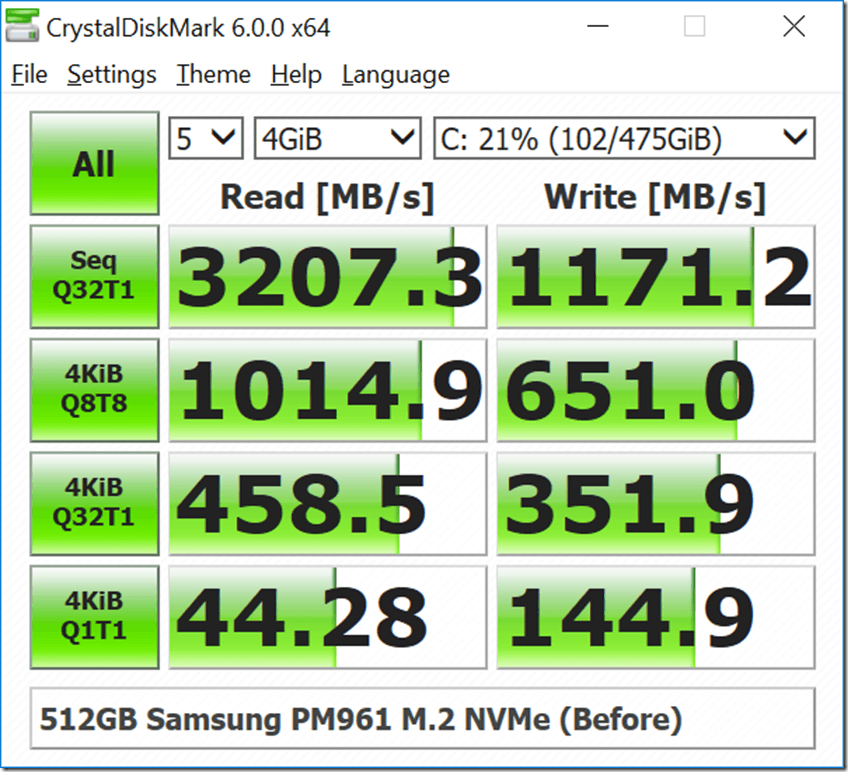
After I had installed the Windows 10 January 2018 Security Update (KB4056892) on this system, I ran both the CPU-Z 1.82.1 CPU benchmark and the CrystalDiskMark 6.0.0 synthetic disk benchmark three times, to get a performance baseline before I installed the new BIOS (that has the microcode update to enable the Spectre variant 2 fixes). Some results from these test runs are shown in Figures 3 and 5 below.
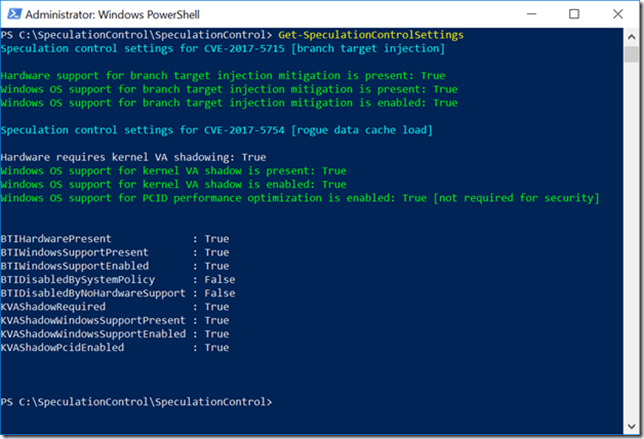
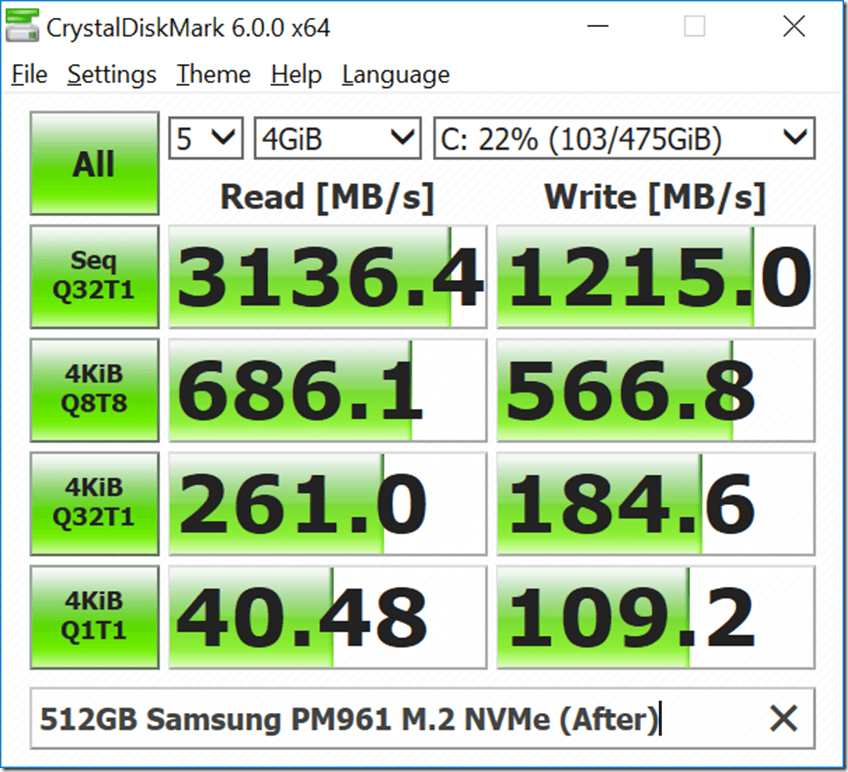
Following Microsoft’s guidance, I located and installed the latest BIOS for my HP Spectre x360 laptop, which is version F.42. Then, I again used PowerShell to check my status, with the results as shown in Figure 2. These are the relevant results:
Speculation control settings for CVE-2017-5715 [branch target injection] (This is Spectre variant 2)
Hardware support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: True
Speculation control settings for CVE-2017-5754 [rogue data cache load] (This is Meltdown)
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: True [not required for security]
Figure 2: After Windows 10 Security Update and BIOS Update
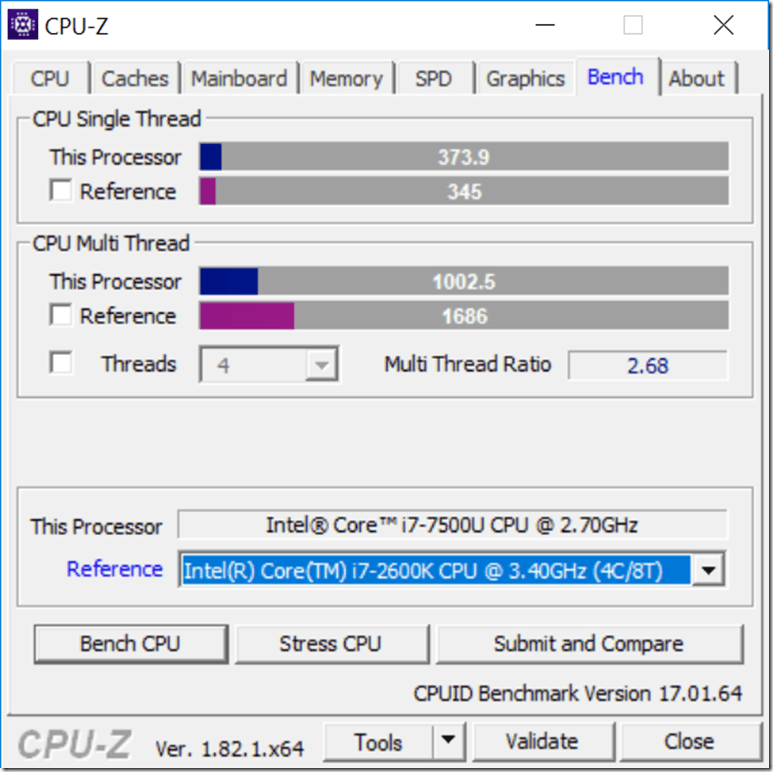
Figure 3 shows one of the CPU-Z 1.82.1 benchmark run results before the BIOS update, showing a CPU Single Thread score of 373.9, and a CPU Multi Thread score of 1000.2.
Figure 3: After Windows 10 Security Update, but before BIOS Update
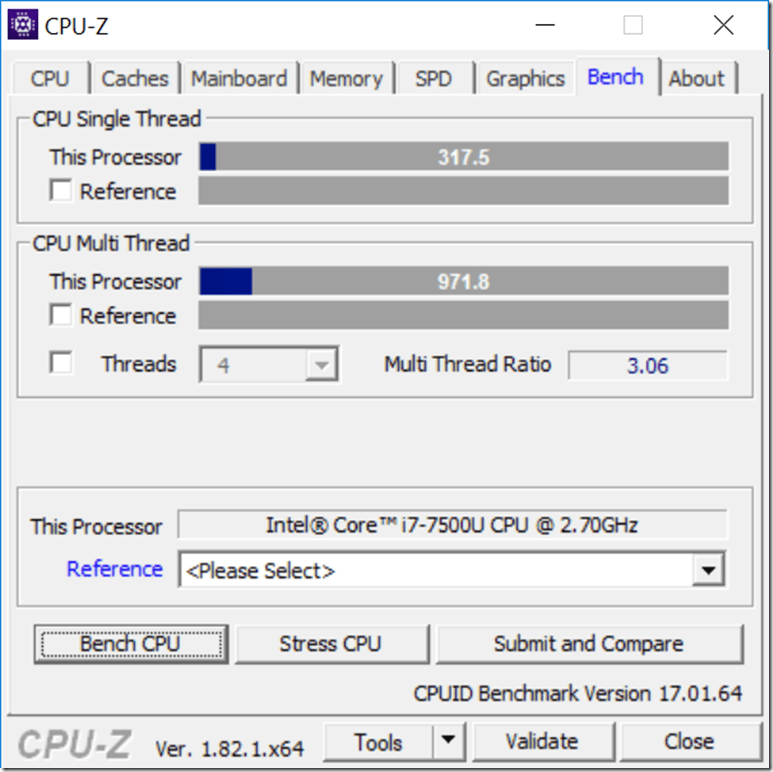
Figure 4 shows one of the CPU-Z 1.82.1 benchmark run results after the BIOS update, showing a CPU Single Thread score of 317.5, and a CPU Multi Thread score of 971.8. That is about a 15.1% reduction in single-threaded CPU performance and a 2.8% reduction in multi-threaded CPU performance, at least on this quick synthetic CPU benchmark.
Figure 4: After Windows 10 Security Update and BIOS Update
Figure 5 shows one of the CrystalDiskMark 6.0.0 benchmark run results before the BIOS update.
Figure 5: After Windows 10 Security Update, but before BIOS Update
Figure 6 shows one of the CrystalDiskMark 6.0.0 benchmark run results after the BIOS update.
Figure 6: After Windows 10 Security Update and BIOS Update
What these limited synthetic benchmark test results show is that installing the CPU microcode updates (which are a required part of the Spectre variant 2 fix) seems to have a pretty significant effect on single-threaded CPU performance in the CPU-Z benchmark. We also see a very significant effect on random I/O performance in CrystalDiskMark 6.0.0 using the default test settings with a 4GB test file.
Microsoft’s Terry Myerson has a pretty detailed post on this subject
Understanding the performance impact of Spectre and Meltdown mitigations on Windows Systems
Intel has published some client benchmark results for 6th, 7th, and 8th Generation Core processors, as shown here:
Intel Security Issue Update: Initial Performance Data Results for Client Systems